Identity Governance is, for many, a grey cloud of uncertainty and misconception where businesses do not understand what it implies, why it is essential, and where to begin. And no wonder. There are today so many different requirements for a company to get a decent cyber defense to stay secure where they can protect their intellectual property (IP), other essential and general data, Identities, and applications where they can ensure business continuity in a world where cybercrime is more and more common. In addition, companies are today migrating on a large scale to cloud-native, hybrid, and multi-cloud infrastructure solutions, adding more layers of complexity.

As most businesses now create and consume data in the cloud, we are no longer protected by the network and traditional firewalls or physical security, nothing new here. Most businesses today know that the Identity is the first line of defense and needs to be protected where more and more companies have introduced Multi-Factor (MFA) and other Identity Security mechanisms; even A.I. is being used today to control and govern access.
But.
What if the person you hire or the consultant you engage is the one causing harm to your infrastructure? Either by mistake or deliberate action. What then? These are one of many scenarios that give the need for proper governance of Identities and not only for privileged users and access but for all users; however, approx. 80% of security breaches involve privileged credentials, so it’s only natural to start with users who have privileged access to the environment and can cause the most harm.
So what is Identity governance, and why is it essential to your business?
Identity Governance is a subset of tools, processes, and operational routines that govern the identity in its life cycle, from birth to death, including change management. Typically Identity Governance will ensure that the identity stays safe and secure throughout its life. At the same time, IT minimizes the risk of the identity harming the environment in that same period, either directly or indirectly, with harmful intent and purpose or by accident. An example of this is always to minimize the time the user has a privileged role by automatically stripping the user of its position after x amount of minutes/hours while IT will monitor this carefully.
Questions you need to be asking are, but not limited to:
- Who is accessing? What is their role? Is the account compromised?
- Where is the user based? From where is the user signing in? Is the IP anonymous?
- Which app is being accessed? What is the business impact?
- Is the device healthy? Is it managed? What is its exposure and attack surface?
- What data is being accessed? Is it classified? Is it allowed off-premises?
- Do we have Oversight of Inactive identities and super identities?
- Do we have Identified Overpermissioned active identities?
- Are we able to visualize Cross-account access?
- How do you detect anomalous behavior among workload identities?
In a series of blog posts, I will break down what Identity Governance is and what you need to succeed in adequately governing your identities with a focus on privileged accounts and access. Being a Microsoft geek working for a Microsoft partner, it’s only natural to focus on their available tools and services. We will look at
- Provisioning and life cycle concepts
- Privileged Identity Management (PIM)
- Permission Management
- Entitlement Management
- Access Reviews
- Conditional Access
- Monitoring and Log Analytics
- Automation
- Cross Cloud Management and B2B
- (Zero-Trust)
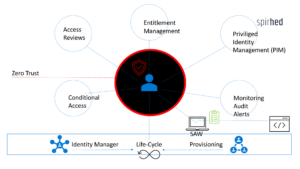
In addition, we will dig into Zero-Trust security and how that also fits into a proper Identity Governance model. So stay tuned for posts to come in the following months.
Please let me know if you have any other thoughts or questions!
Stay safe and secure

