In this blog post I will easy and quickly summarize how you can setup a Cross domain Failover Cluster Replication with some self signed Certificates.
Let’s get some context.
You have 2 domains, DomainA.local(Source) and DomainB.local(Destination for Replica).
Each domain has some Hyper-V servers in a cluster. For Hyper-V replica across domains to work we need to use Certificates.
If you have a certificate Authority you can use that to generate some certs. But as you will need 2 different domain certs from same RootCA the best way is to use a self signed certificate.
To create the certificate we will use Makecert.exe that comes with Windows SDK. You can find it here, and some info on how to use it.
First we need some certs, on a computer, does not matter which one run the following commands when you have downloaded the SDK and installed the certificate components. Create them under c:\temp . You can find the makecert under C:\Program Files\Microsoft SDKs\Windows\v7.1\Bin
Create Certs for replication
1. Create the Main Root Cert
We can do this with Makecert(Not available anymore) and
New-SelfSignedCertificate
makecert.exe -pe -n “CN=MyLocalCA” -ss root -sr LocalMachine -sky signature -r “MyLocalCA.cer”
$params = @{
DnsName = "MyLocalCA"
KeyLength = 2048
KeyAlgorithm = 'RSA'
HashAlgorithm = 'SHA256'
KeyExportPolicy = 'Exportable'
NotAfter = (Get-Date).AddYears(5)
CertStoreLocation = 'Cert:\LocalMachine\My'
KeyUsage = 'CertSign','CRLSign' #fixes invalid cert error
}
$rootCA = New-SelfSignedCertificate @params
2. Now we need to create a Certificate for the Source Domain
makecert.exe -pe -n “CN=*.DomainA.local” -ss my -sr LocalMachine -sky exchange -eku 1.3.6.1.5.5.7.3.1,1.3.6.1.5.5.7.3.2 -in “MyLocalCA” -is root -ir LocalMachine -sp “Microsoft RSA SChannel Cryptographic Provider” -sy 12 wildcard.DomainA.local.cer
$params = @{
DnsName = "*.DomainA.local"
Signer = $rootCA
KeyLength = 2048
KeyAlgorithm = 'RSA'
HashAlgorithm = 'SHA256'
KeyExportPolicy = 'Exportable'
NotAfter = (Get-date).AddYears(2)
CertStoreLocation = 'Cert:\LocalMachine\My'
}
$vpnCert = New-SelfSignedCertificate @params
3. Then we need to make a cert for the Replica Destination Domain
makecert.exe -pe -n “CN=*.DomainB.local” -ss my -sr LocalMachine -sky exchange -eku 1.3.6.1.5.5.7.3.1,1.3.6.1.5.5.7.3.2 -in “MyLocalCA” -is root -ir LocalMachine -sp “Microsoft RSA SChannel Cryptographic Provider” -sy 12 wildcard.DomainB.local.cer
$params = @{
DnsName = "*.DomainB.local"
Signer = $rootCA
KeyLength = 2048
KeyAlgorithm = 'RSA'
HashAlgorithm = 'SHA256'
KeyExportPolicy = 'Exportable'
NotAfter = (Get-date).AddYears(2)
CertStoreLocation = 'Cert:\LocalMachine\My'
}
$vpnCert = New-SelfSignedCertificate @params
4. Now let’s export the 2 wildcard certificates, from your local certificate store. So open MMC and add certificate snapin. We will need the Private Key and the extended key’s. Save them as pfx and create a password.
5. Copy the wildcard.DomainA.local.pfx and MyLocalCA.cer cert to each Hyper-V hosts in the source domain
6. Then import the wildcard.DomainA.local cert on each Hyper-V host in the source domain. Use the following commands
$Pass = "Password" $password = ConvertTo-SecureString $Pass -AsPlainText -Force Import-PfxCertificate -FilePath "Path to file" -CertStoreLocation Cert:\LocalMachine\My -Password $password
7. Once the PFX cert is installed import the MyLocalCA.cer cert to the trusted root store as well.
Import-Certificate -FilePath "Path to file" -CertStoreLocation Cert:\LocalMachine\Root
8. As these are selfsigned cert’s we need to turn of Certificate Revocation list for the Hyper-V and Failover Replication feature. Run these commands on the Hyper-V Hosts
reg add “HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Virtualization\FailoverReplication” /v DisableCertRevocationCheck /d 1 /t REG_DWORD /f reg add “HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Virtualization\Replication” /v DisableCertRevocationCheck /d 1 /t REG_DWORD /f
9. Now let’s copy over the wildcard.Domainb.local.pfx and MyLocalCA.cer cert to each Hyper-V host in the Destination domain.
10. Then import the wildcard.DomainB.local cert on each Hyper-V host in the source domain. Use the following commands
$Pass = "Password" $password = ConvertTo-SecureString $Pass -AsPlainText -Force Import-PfxCertificate -FilePath "Path to file" -CertStoreLocation Cert:\LocalMachine\My -Password $password
11. Once the PFX cert is installed import the MyLocalCA cert to the trusted root store as well
Import-Certificate -FilePath "Path to file" -CertStoreLocation Cert:\LocalMachine\Root
12. As these are selfsigned cert’s we need to turn of Certificate Revocation list for the Hyper-V and Failover Replication feature. Run these commands on the Hyper-V Hosts
reg add “HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Virtualization\FailoverReplication” /v DisableCertRevocationCheck /d 1 /t REG_DWORD /f reg add “HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Virtualization\Replication” /v DisableCertRevocationCheck /d 1 /t REG_DWORD /f
13. Now we can start with setting up the replication.
Configuring the Replication
In a Failover Cluster scenario we need to configure the Hyper-V Replica Broker role. This needs to be done on both source and destination if it’s a Failover Cluster.
To do so go to the Failover Cluster Manager and right click on roles and Click on configure roles
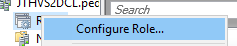
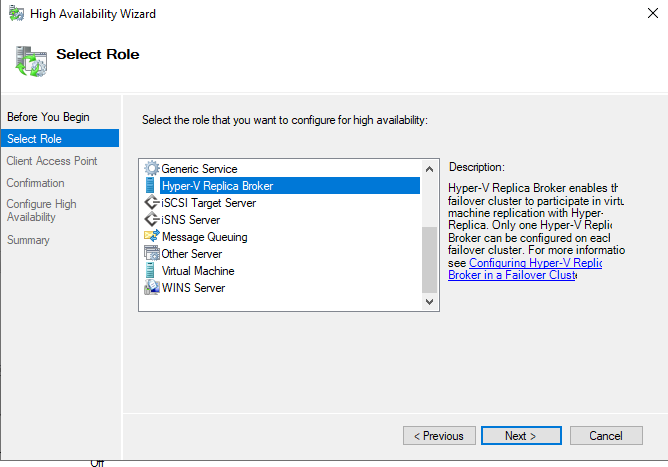
Then select the Hyper-V Replica Broker Role
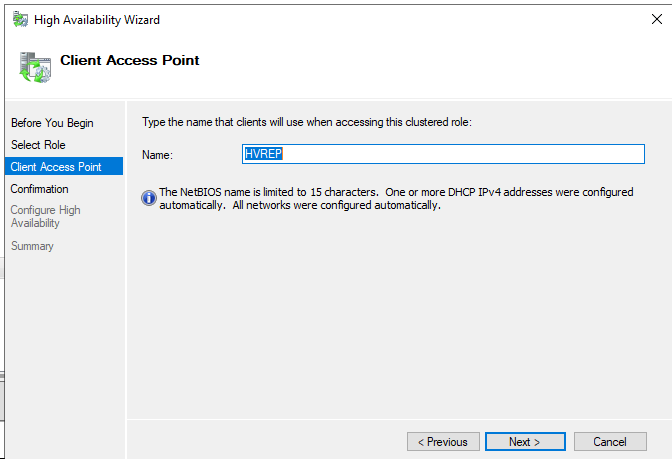
Set a name for the replica role, i recommend to prestage the name in the same OU as the Hyper-V nodes and Cluster name is and give the cluster full access to it. If not the role will not come online.
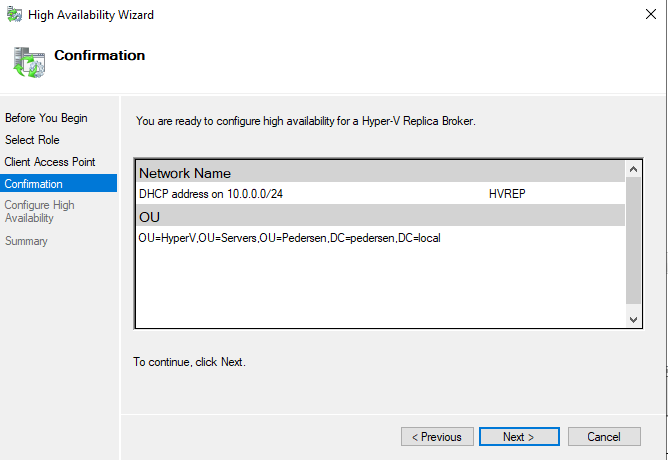
Click next and let it finish.
Right click on the new role and choose Replication Settings
Enable replication, set the destination to where the incomming replications should go. You can choose a single path or 1 path pr server.
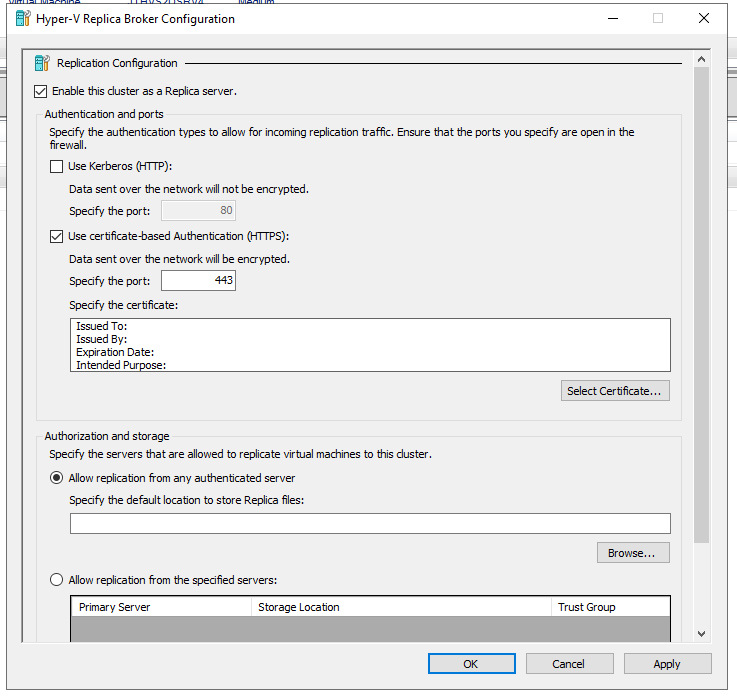
Choose Use Certificat-Based and click on select certificate. If there is no valid certificate you will get this error msg.
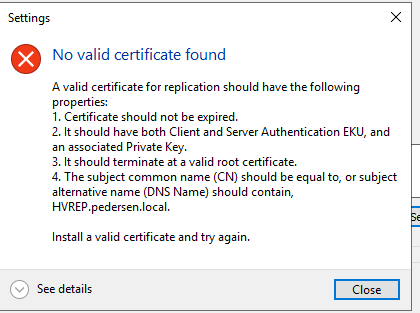
But as you have followed my guide you will get a cert to use. Now repeat for all clusters you want to replicate between.
For standalone nodes, you go into the Hyper-V manager and choose the replication page there. And do the same as above.

