In this blog post i will show you how to setup a Microsoft VPN connection with the new NPS Extension for Azure AD MFA.
This is new service that the Microsoft NPS team just released, that adds an Extension to the Windows Network Policy Server.
When using the NPS extension for Azure MFA, the authentication flow includes the following components:
This is copied from https://docs.microsoft.com/nb-no/azure/multi-factor-authentication/multi-factor-authentication-nps-extension
- NAS/VPN Server receives requests from VPN clients and converts them into RADIUS requests to NPS servers.
- NPS Server connects to Active Directory to perform the primary authentication for the RADIUS requests and, upon success, passes the request to any installed extensions.
- NPS Extension triggers a request to Azure MFA for the secondary authentication. Once the extension receives the response, and if the MFA challenge succeeds, it completes the authentication request by providing the NPS server with security tokens that include an MFA claim, issued by Azure STS.
- Azure MFA communicates with Azure Active Directory to retrieve the user’s details and performs the secondary authentication using a verification method configured to the user.
The following diagram illustrates this high-level authentication request flow:
How to setup
First setup 2 new servers, one installed with the NPS service. And the other installed with the Remote Access service with DirectAccess and VPN installed. Make sure the VPN server has a WAN interface or similar that is accessible via a firewall and make sure that one has the default route.
Azure MFA Setup
I will refer you to Freek Berson’s post about the RDPGW setup and the Azure Setup here. As you will see most of the setup is identical when it comes to the NPS part of this setup.
One thing to note. The NPS Extension does only work with the mobile app with receive notifications for verification and phone call.
To the servers
The VPN server
Once the install of the Remote Access service is done it will open a wizard. Click on Deploy VPN Only
This will open the Routing and Remote Access page
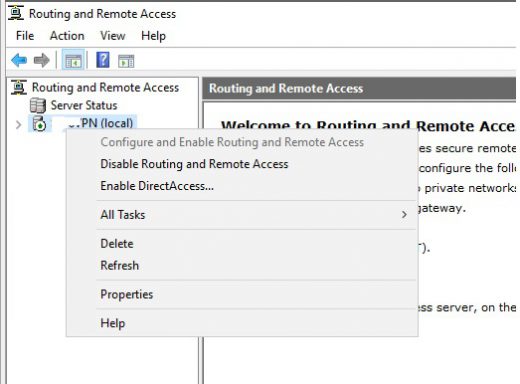
Right click the server name and click on Configure and enable Routing and Remote Access
Click on Custom Configuration
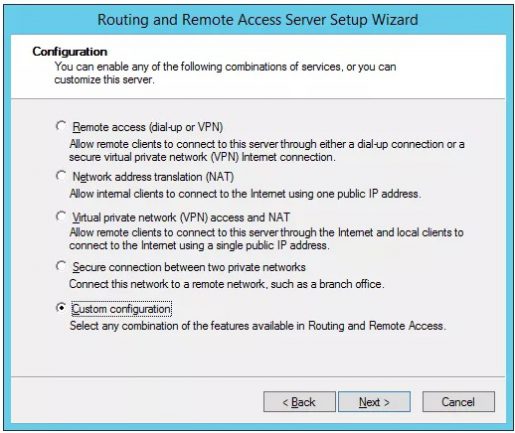
Select VPN Access
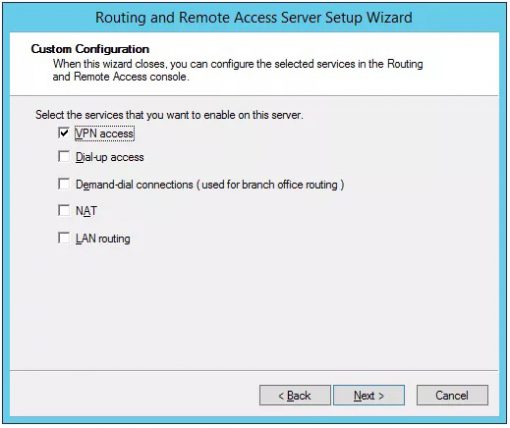
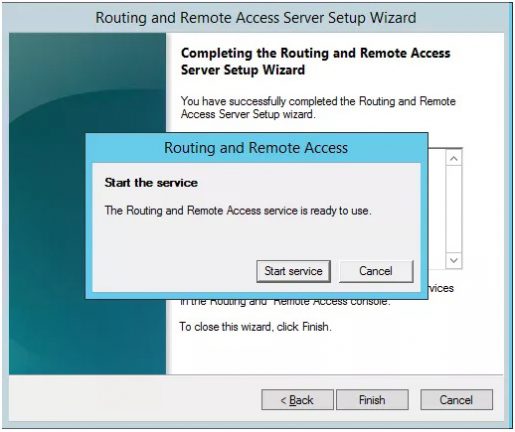
Click next and start the routing and remote access service
Make sure your users are enabled for Network Access Permission in the dial-in tab in Active Directory
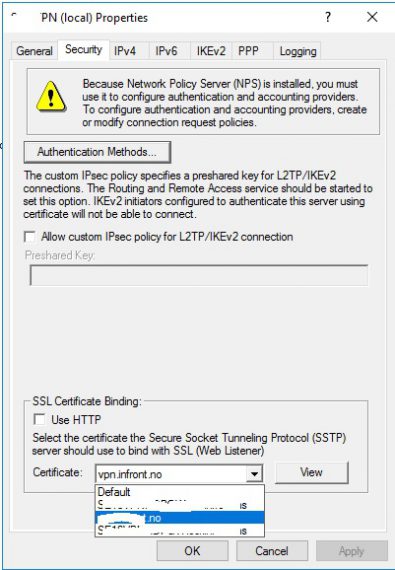
Now let’s configure a certificate on the server.
Install a public or internal certificate corresponding to the DNS name you will be using. For a public DNS use a certificate from digicert or any other provider.
Right click the server name and click properties
Click on the Security Tab and choose a certificate at the bottom. Then click ok
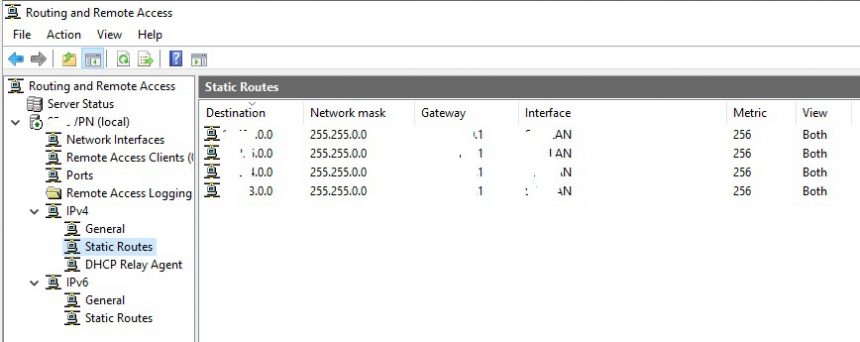
Now drill down to IP4 and Static Routes and define any static routes if you need to.
Now let’s move to the NPS part of the VPN server.
Open up the network and policy server.
Let’s start with configuring a Radius client, right click on radius clients and click new.
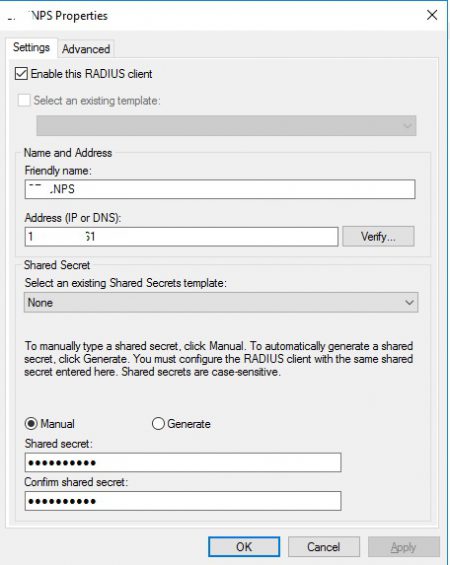
Enter a name and IP adress of the NPS server, and type in a shared secret. Write this down as we will use it again 3 more times.
Now right click Remote radius server and click new
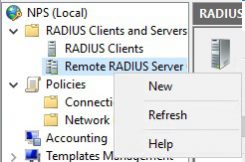
Click on add and fill out ip address for NPS server
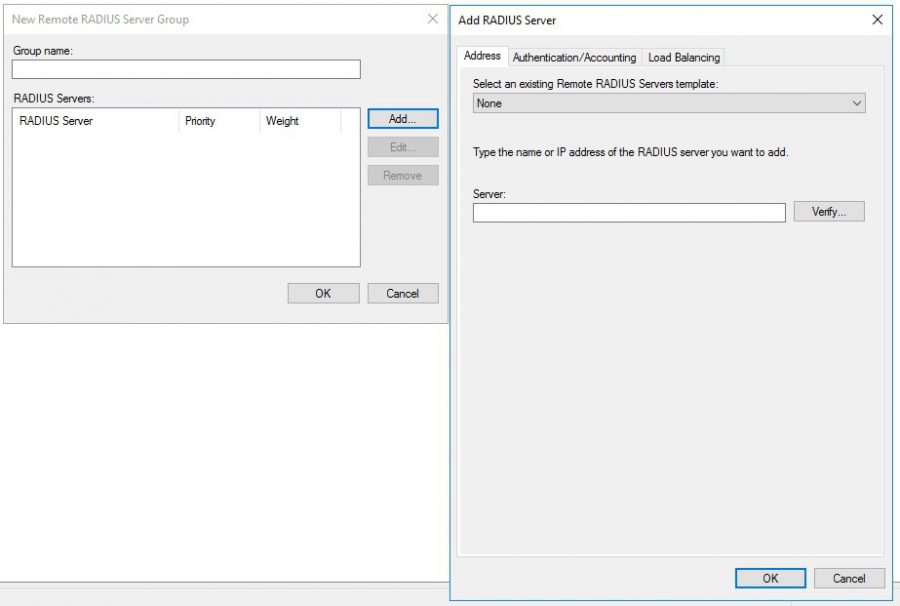
Click on Authentication/accounting tab and enter the shared secret you wrote down before
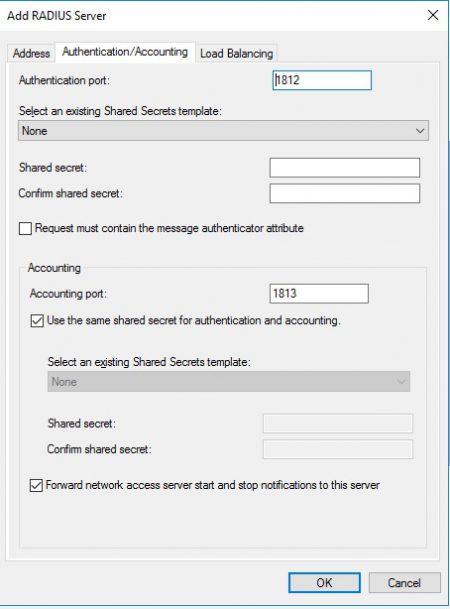
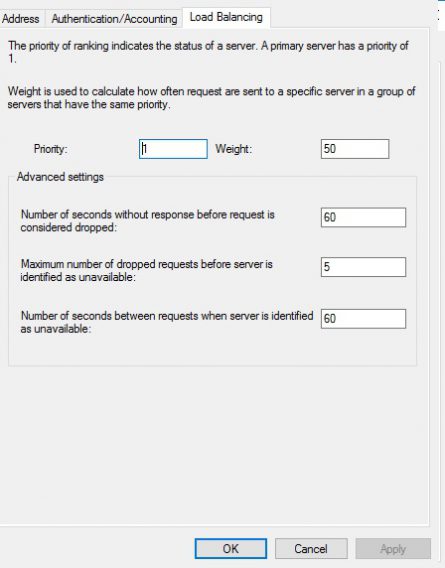
Now go to the load balancing tab and change values to reflect picture below
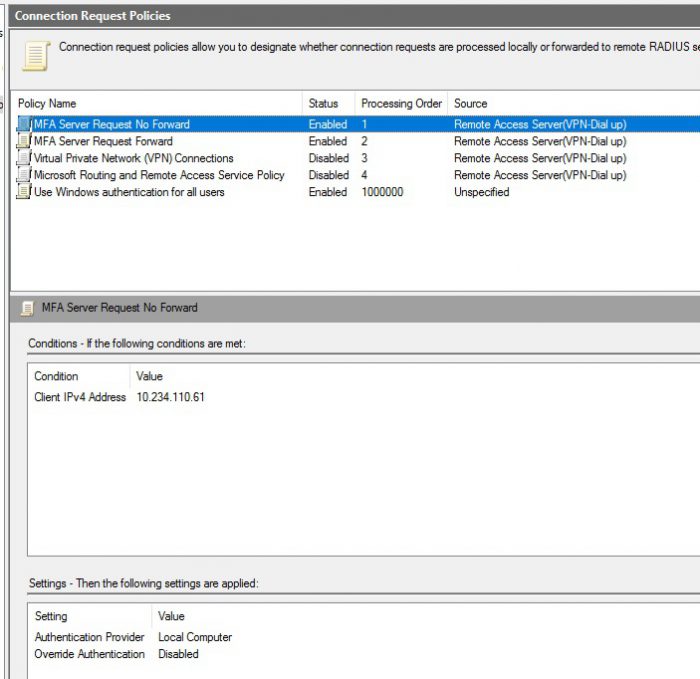
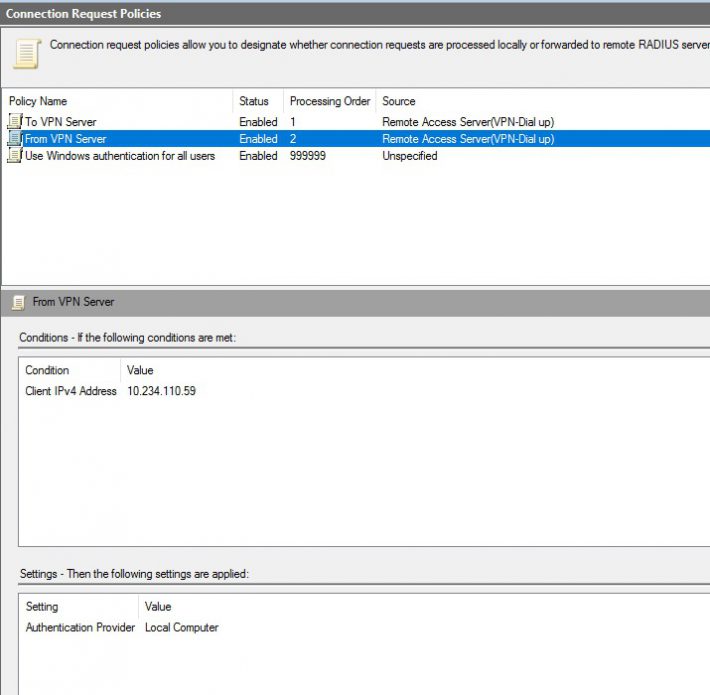
Now go to Connection Request Policies and create the 2 rules in the picure below, make sure they are in the correct order. Right click and click new.
Client IPv4 is the ipadress of the NPS server. Make sure the policy is enabled.
On the second one create a nas port and set the providers to the NPS server that was defined in the Remote Radius Server
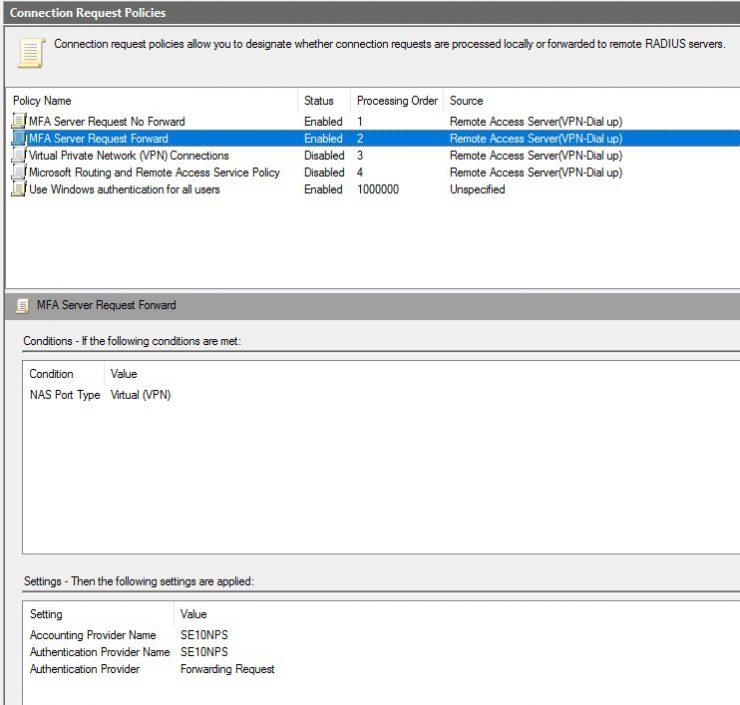
Now disable Virtual Private Network (VPN) Connections and Microsoft Routing and Remote Access Service Policy as you can see in the picture above.
Now create a network policy, right click and click new. It should be similar to the picture. I have defined a domain group to allow login.
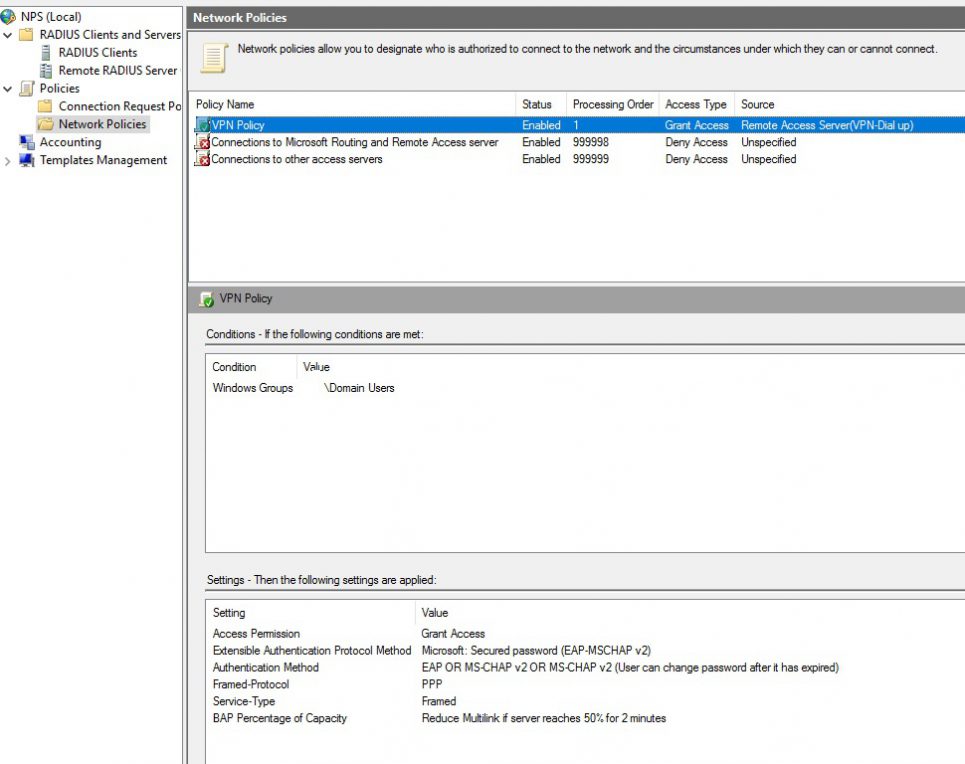
Now we are done on the VPN server
To configure the NPS Server
Install Visual Studio 2013 c++ Redistributable (X64) you can download it here.
Install Microsoft Azure Active Directory Module for Windows Powershell you can download it here.
Install the NPS extension for Azure MFA you can download it here.
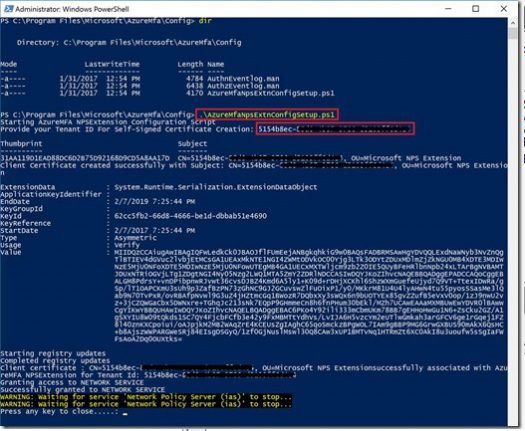
Once it’s installed open powershell and go to C:\Program Files\Microsoft\AzureMfa\ then run the script AzureMfaNpsExtnConfigSetup.ps1
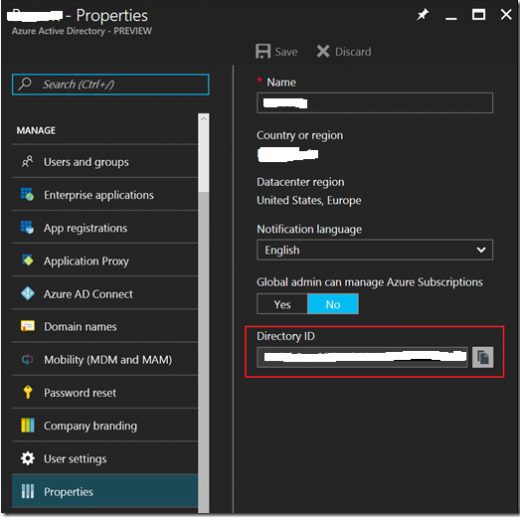
Now you will need your tennant ID from Azure to add into powershell once the script asks for it.
You will find it under active directory and properties in the azure portal.
Now let’s open NPS on the NPS server
Let’s add the VPN server as a radius client. Add a new and enter the ip address of the VPN server and the shared secret we used before
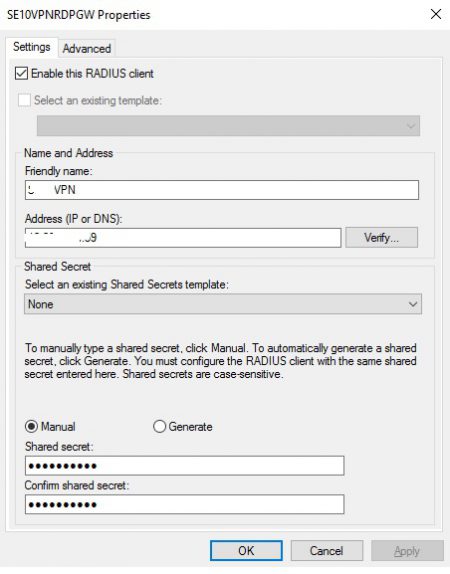
Now let’s add a Remote Radius server, click new and add the info for the VPN server, The ip address, add the shared secret on the authentication tab as before and on the load balancing add the correct settings.


Now let’s add a 2 connection request policies. Mirror them to mine. For the To VPN Server set the NAS port to VPN and the providers to the Remote Radius Server
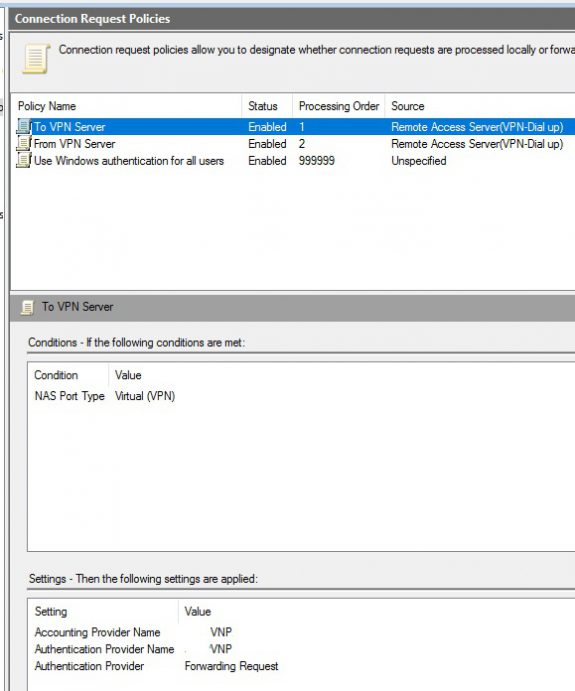
On the From VPN Server set the IPv4 the ip off the vpn server.
And we are done
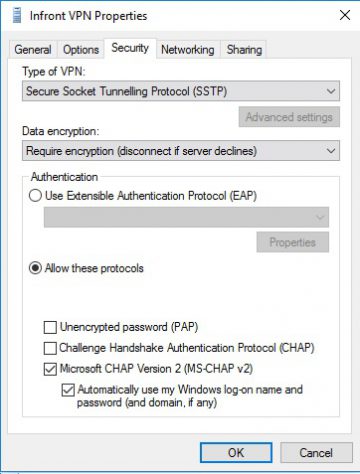
Now set your vpn in windows to thes settings. And you should be fine.

19 thoughts on “Setup VPN to use MFA with NPS Extension”
Thanks for this guide, just what i was looking for.
I do have a question about DirectAccess since i have 1 server installed with DirectAccess and VPN and want to utilize MFA with the NPS extension, is that possible or it will destroy Directaccess once installed and configured on the VPN side.
Regards
Poul
Hello
I have not done this via Direct Access. But could work. If it’s a VM you can just create a snapshot to revert to if it does not work.
Regards
Jan-Tore
Thanks for this guide, just what i was looking for.
I do have a question about DirectAccess since i have 1 server installed with DirectAccess and VPN and want to utilize MFA with the NPS extension, is that possible or it will destroy Directaccess once installed and configured on the VPN side.
Regards
Poul
Hello
I have not done this via Direct Access. But could work. If it’s a VM you can just create a snapshot to revert to if it does not work.
Regards
Jan-Tore
This is great write up. Very helpful.
I am confused by the references to the NPS Server(s).
Is the RAS server also an NPS server? That is the one with the Connection policies of MFA Forward and No Forward, correct?
And then there is the 2nd NPS server, which has the Azure MFA extension installed on it. Correct?
Thanks
John
That is correct, need 2 NPS, one installed on the VPN/RAS server and a 2nd NPS for the MFA extension.
Thanks
JT
This is great write up. Very helpful.
I am confused by the references to the NPS Server(s).
Is the RAS server also an NPS server? That is the one with the Connection policies of MFA Forward and No Forward, correct?
And then there is the 2nd NPS server, which has the Azure MFA extension installed on it. Correct?
Thanks
John
That is correct, need 2 NPS, one installed on the VPN/RAS server and a 2nd NPS for the MFA extension.
Thanks
JT
Hi, We have 3 VPN servers and 3 NPS servers (Load balanced) and setup Azure MFA extension. The VPN server 1 works great with all the Load balanced NPS server for both IKEv2 and SSTP, but for the other 2 VPN server works only for SSTP, The setup works good if we uninstall the extension on the NPS servers.
go trough the setup on the other 2 setups and check against the one that is working. something must be wrong configured.
Hi, We have 3 VPN servers and 3 NPS servers (Load balanced) and setup Azure MFA extension. The VPN server 1 works great with all the Load balanced NPS server for both IKEv2 and SSTP, but for the other 2 VPN server works only for SSTP, The setup works good if we uninstall the extension on the NPS servers.
go trough the setup on the other 2 setups and check against the one that is working. something must be wrong configured.
This is a great writeup. I’m trying my own setup, and I think I followed all the steps in your article, but when I try to connect my VPN, there is a considerable pause veryifing username and password and then I get an error 718. Any sugestions to troubleshoot this?
Sorry i have not seen this issue. Have you googled the issue?
This is a great writeup. I’m trying my own setup, and I think I followed all the steps in your article, but when I try to connect my VPN, there is a considerable pause veryifing username and password and then I get an error 718. Any sugestions to troubleshoot this?
This is very useful article.
Is there any post regarding azure mfa and nps server internal workflow?
No sorry there is not. This should be the best way to describe it. https://docs.microsoft.com/en-us/azure/active-directory/authentication/howto-mfa-nps-extension
This is very useful article.
Is there any post regarding azure mfa and nps server internal workflow?
No sorry there is not. This should be the best way to describe it. https://docs.microsoft.com/en-us/azure/active-directory/authentication/howto-mfa-nps-extension